Update, Dec. 1, 2011: False alarm! Well, at least in the Illinios water pump case. Read this Wired | Threat Level article for the real story. Still, no reason to let your guard down…
This weekend, hackers made news for not only breaking into computer systems, but literally breaking a pump at a water plant in Illinois. Hackers were able to damage a pump at the Curran-Gardner Township Public Water District in Illinois by cycling it on and off remotely. Thanks to redundancies, service was unaffected.
While the FBI and DHS look into the matter, computer security experts are sounding the alarm and stressing the need to harden the SCADA (Supervisory Control and Data Acquisition) systems that operate the nation’s infrastructure.
Stuxnet casts an imposing shadow
One of the more troubling aspects of this attack is how it’s believed to have been carried out. Initially, Stuxnet — or malware like it, such as Duqu — was suspected. Stuxnet is responsible for interfering with Iranian nuclear power sites and fouling things up at utilities in other parts of the world. Since last year, the worry was that this could become a template for crippling critical infrastructure here in the United States. Needless to say, it’s also a huge warning sign as the next generation of IT-rich smart power grids are brought online.
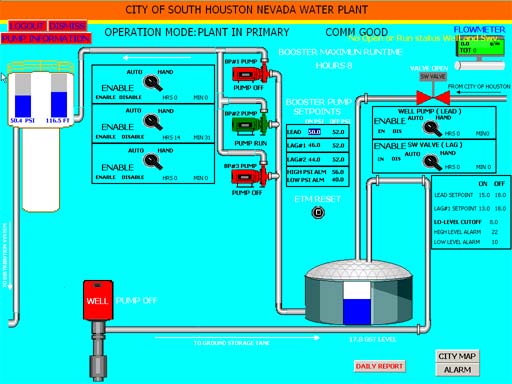
Alas, as scary as Stuxnet is, the attack may have been more ‘basic’ according to pr0f, a hacker that accessed a separate water treatment facility in South Houston.
Countering an underwhelming response to the Illinois incident from the DHS, pr0f details how lax security practices and connecting critical systems to the Internet with weak protections can be the undoing of utility control systems in this Pastebin entry.
…No damage was done to any of the machinery; I don’t really like mindless vandalism. It’s stupid and silly.
On the other hand, so is connecting interfaces to your SCADA machinery to the Internet. I wouldn’t even call this a hack, either, just to say. This required almost no skill and could be reproduced by a two year old with a basic knowledge of Simatic.
As proof, the post contains several SCADA screen captures from a water facilities in South Houston one of which is pictured at the top of this post. Now imagine an image of your desktop posted online by a hacker. Chilling, right?
Thwarting basic hacks with basic security
This is a wake-up call. While malware like Stuxnet and Duqu are scary, it’s more scary to think that utilities and their SCADA providers aren’t subscribing to the same standards that govern computer security in most businesses, government agencies and organizations. And it’s not that they ever get hacked, right?
While it might be eye-rollingly obvious to techies in the trenches of corporate IT, Dave Marcus, Director of Security Research for McAfee Labs, dispenses some great advice for SCADA admins. Stuff like setting up extensive penetration testing and counter-social engineering training.
Again, it’s basic stuff. But given how trivially pr0f penetrated that water plant, the basics are a big improvement at this stage.
Image credit: pr0f

Leave a Reply